May 22, 2025
How to Secure XML Data: Encryption and Digital Signatures
Today's interlinked world requires data protection, especially online. XML data storage and system connectivity make it an excellent fraud target. Financial transactions, cloud storage, and web services risk unauthorized access or data manipulation. Don't worry, this post will show you two vital XML data security methods: Digital signatures and XML encryption.
Understanding the Risks of XML Data
XML is versatile and strong, but not secure. Interception, manipulation, and illegal access are possible when sent online or stored on servers. Without sufficient security, credit card, personal, and corporate data may be at danger. Even with HTTPS, someone may view your XML file if they intercept the request or get server access.
Digital signatures and encryption help here. To mitigate these dangers, they keep XML data secret, genuine, and tamper-proof.
Introduction to XML Encryption
Strong XML encryption protects sensitive data in XML documents. In contrast to file or transport layer encryption, XML encryption targets the data. You may encrypt XML components, documents, or attributes. This safety measure prohibits unauthorized users from accessing sensitive XML information, even if they access the document.
XML-ENC standards encrypt hierarchically structured XML data. If you encrypt an XML document with a name and credit card number, only authorized people may see it. This keeps the rest of the document available for efficiency and security.
How to Implement XML Encryption
Implementing XML encryption is easy with the correct tools and libraries. Several programming languages use safe AES encryption.
Let's explain XML data encryption. Generate a symmetric encryption key first. This key encrypts and decrypts data. Encrypting the sensitive sections of the XML document ensures that only the keyholder can read the original information.
A simple Python example utilizing PyCryptodome, which simplifies AES encryption:
from Crypto.Cipher import AES
from Crypto.Random import get_random_bytes
from lxml import etree
# Generate a random AES key
key = get_random_bytes(16)
cipher = AES.new(key, AES.MODE_EAX)
# XML data
xml_data = '<person><name>John Doe</name><ccn>1234-5678-9876-5432</ccn></person>'
# Encrypt the credit card number element
encrypted_data, tag = cipher.encrypt_and_digest(xml_data.encode())
# Output encrypted data
print(encrypted_data)
Key management and storage are important for preventing unauthorized decryption. Hardware security modules (HSM) and cloud key management services (KMS) can safeguard encryption keys in real life.
Introduction to Digital Signatures for XML
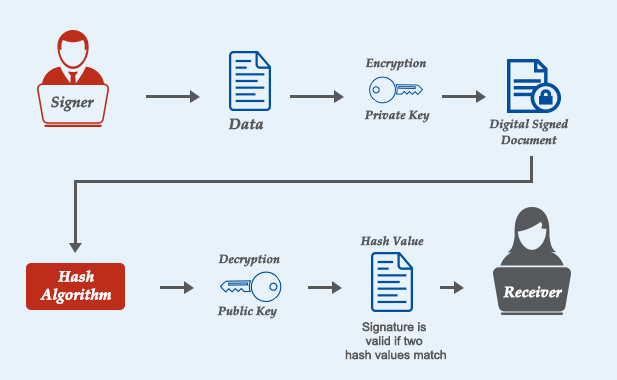
Encryption protects data but not its source or validity. Introducing digital signatures. Digital signatures use cryptography to verify data integrity. It verifies the sender and integrity of the XML data.
Digital signatures generate an XML document hash and sign it with a private key. The receiver may use the public key to verify the signature, assuring no data modification.
How to Implement Digital Signatures for XML
The implementation of digital signatures requires multiple phases. First, hash the XML document. This hash uniquely identifies the document. Sign the hash using your private key to create a digital signature. The receiver may use your public key to verify the signature and check for changes.
A basic Python example using xmlsec to digitally sign an XML document:
import xmlsec
from lxml import etree
# Load the XML document
doc = etree.parse("document.xml")
# Load the private key (use a secure method to store keys in production)
private_key = xmlsec.Key.from_file("private_key.pem", xmlsec.KeyFormat.PEM)
# Create the signature
signer = xmlsec.Signature()
signer.sign(doc, private_key)
# Save the signed document
doc.write("signed_document.xml")Receiving side uses public key to verify signature. A successful verification procedure ensures document integrity.
Combining Encryption and Digital Signatures
XML encryption and digital signatures are beneficial, but combining them provides total security. Digital signatures authenticate data validity and encryption protects it. These solutions protect XML data during transfer or storage.
Imagine a bank delivering customer transaction data. To validate the financial institution's origin and legitimacy, encryption and signing protect consumer personal and financial information. Perfect security comes from encryption and digital signatures.
Conclusion
Today's digital world requires XML data security, particularly for sensitive data. You may secure your data using XML encryption and digital signatures. Secure data transfers need secrecy, authenticity, and integrity, which these methods give. I recommend using these strategies to protect your data and increase user confidence in your apps.
771 views
