Published on November 21, 2025
USEFUL LINUX COMMANDS
USEFUL LINUX COMMANDSCommandDescriptionhostnamectlCheck the Linux version (e.g.,...
Read more...
938 Views

Published on November 04, 2025
Decentralized Finance (DeFi): Harnessing Blockchain for Transparent and Resilient Financial Systems
Decentralized Finance (DeFi): Harnessing Blockchain for Transparent and Resilien...
Read more...
780 Views
Published on November 03, 2025
Building Scalable Web3 Applications: How Blockchain Powers DeFi, Supply Chain, and Digital Identity
Building Scalable Web3 Applications: How Blockchain Powers DeFi, Supply Chain, a...
Read more...
708 Views

Published on October 31, 2025
Multi-Cloud Management for Developers: Optimising Code for Cost Efficiency and Flexibility
Multi-Cloud Management for Developers: Optimising Code for Cost Efficiency and F...
Read more...
765 Views
Published on October 30, 2025
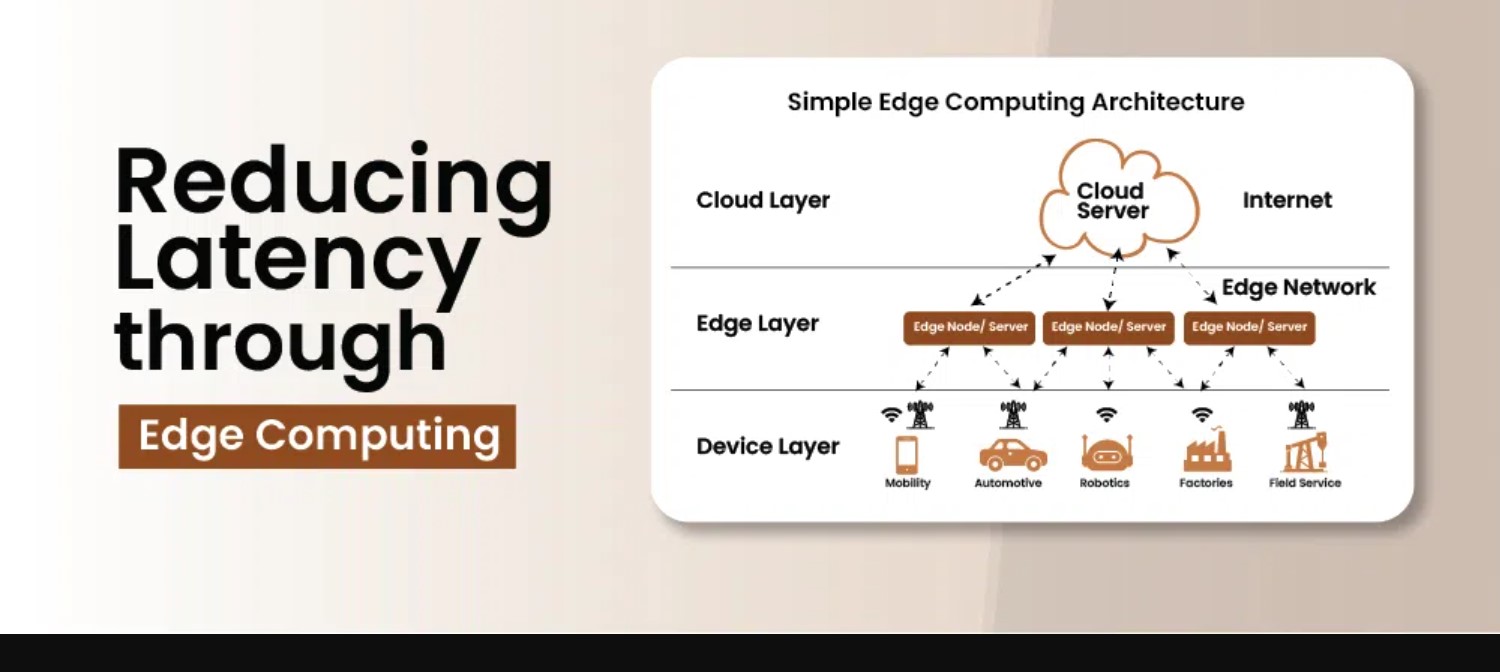
Mastering Edge Computing: A Developer's Guide to Reducing Latency and Optimizing Data Flow
Mastering Edge Computing: A Developer's Guide to Reducing Latency and Optimizing...
Read more...
730 Views

Published on October 29, 2025
Cloud Sovereignty and the Future of Data Governance in Multi-Cloud Systems
Cloud Sovereignty and the Future of Data Governance in Multi-Cloud SystemsEver w...
Read more...
735 Views

Published on October 28, 2025
Mitigating Third-Party Risks: Enhancing Security Protocols for Vendor and Supply Chain Management
Mitigating Third-Party Risks: Enhancing Security Protocols for Vendor and Supply...
Read more...
715 Views
Published on October 27, 2025
Post-Quantum Cryptography: Developing Encryption Methods for Future-Proof Cybersecurity
Post-Quantum Cryptography: Developing Encryption Methods for Future-Proof Cybers...
Read more...
761 Views
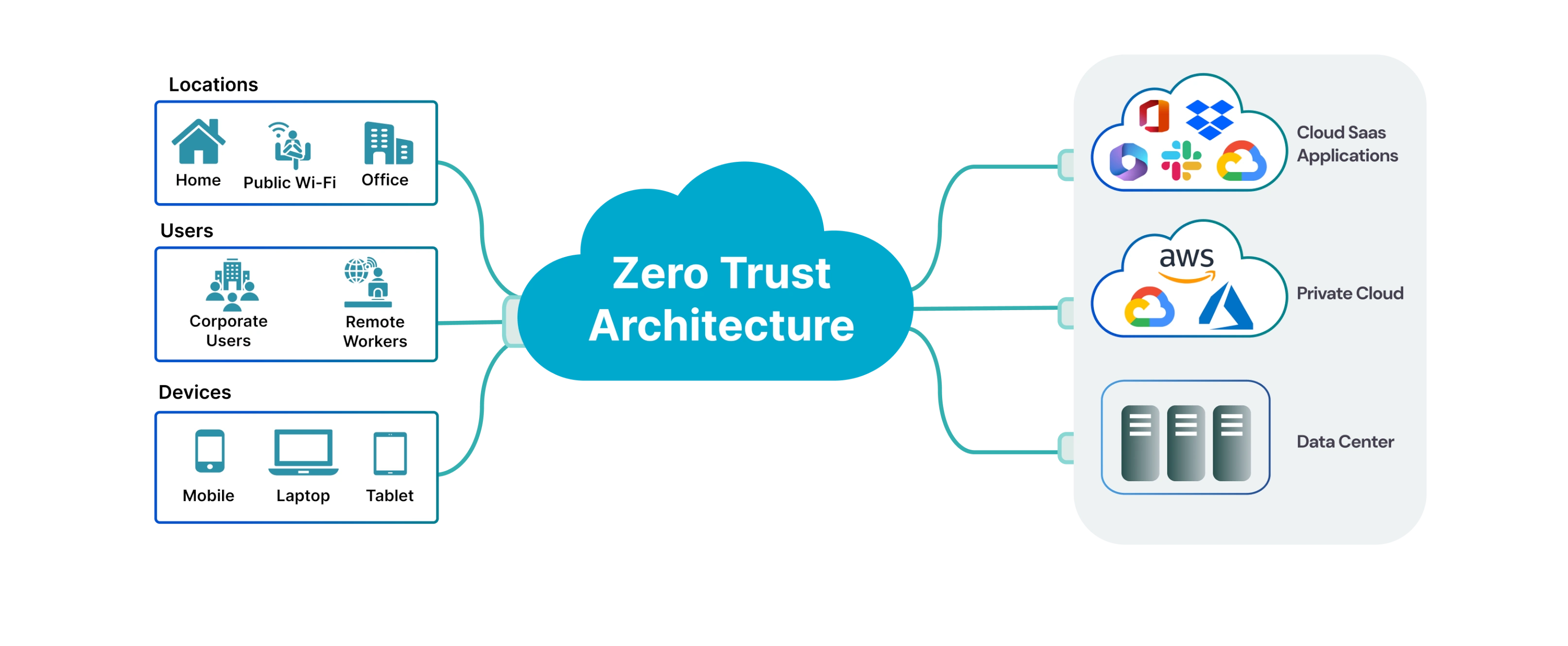
Published on October 24, 2025
Implementing Zero-Trust Architecture: Strengthening Network Security with Continuous Authentication
Implementing Zero-Trust Architecture: Strengthening Network Security with Contin...
Read more...
769 Views

Published on October 23, 2025
Building Operational Resilience: Ensuring Business Continuity Post-Cybersecurity Breach
Building Operational Resilience: Ensuring Business Continuity Post-Cybersecurity...
Read more...
762 Views

